Malware analysis Malicious activity
Por um escritor misterioso
Last updated 22 março 2025
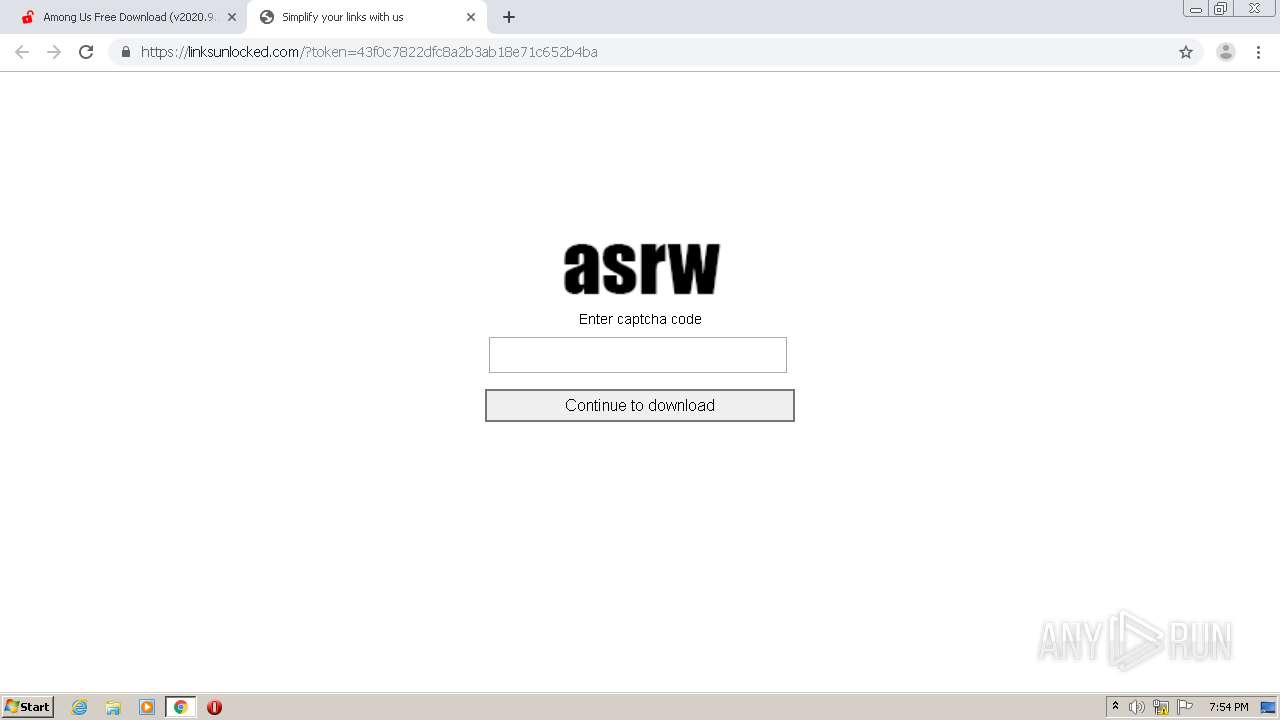

Malware Analysis: Steps & Examples - CrowdStrike

What to Include in a Malware Analysis Report
Malicious URL Scanner, Scan URLs for Malware

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1 · Arch Cloud Labs

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights

Cybersecurity Search Engine
Download Free Antivirus Software

Info stealers and how to protect against them

Malware Analysis: Steps & Examples - CrowdStrike

Malware Analysis: Steps & Examples - CrowdStrike

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable
Malware analysis cd53fba6ddd4ae4ef7a5747c6003236c85791477854cc1b7ce00e0f8ee7677d9 Malicious activity
Recomendado para você
-
 Clicked download on the upload haven from steamunlocked, and it is not working :/ , download is not even starting any idea why and how to solve : r/PiratedGames22 março 2025
Clicked download on the upload haven from steamunlocked, and it is not working :/ , download is not even starting any idea why and how to solve : r/PiratedGames22 março 2025 -
SteamUnlocked - Unlock The Steam22 março 2025
-
 Everything You Need to Know Before Using SteamUnlocked - VPNProfy22 março 2025
Everything You Need to Know Before Using SteamUnlocked - VPNProfy22 março 2025 -
 Unlock the World of Free PC Gaming! by Steam Unlocked - Issuu22 março 2025
Unlock the World of Free PC Gaming! by Steam Unlocked - Issuu22 março 2025 -
 900+ Steamunlocked ideas in 2023 free download, puzzle solving, space sounds22 março 2025
900+ Steamunlocked ideas in 2023 free download, puzzle solving, space sounds22 março 2025 -
 Is Steam unlocked legit and safe? • TechBriefly22 março 2025
Is Steam unlocked legit and safe? • TechBriefly22 março 2025 -
 Pin on SteamUnlocked22 março 2025
Pin on SteamUnlocked22 março 2025 -
 Is Steamunlocked Safe and Legit to use in 2022?22 março 2025
Is Steamunlocked Safe and Legit to use in 2022?22 março 2025 -
 Steamunlocked Site For Free Games - Steam Unlocked - Medium22 março 2025
Steamunlocked Site For Free Games - Steam Unlocked - Medium22 março 2025 -
 What is SteamUnlocked? Is it legit and safe for downloading games?22 março 2025
What is SteamUnlocked? Is it legit and safe for downloading games?22 março 2025
você pode gostar
-
Game Boy Advance - Sonic the Hedgehog Genesis - Sonic - The Spriters Resource22 março 2025
-
 Home Thebackroomscoin22 março 2025
Home Thebackroomscoin22 março 2025 -
 WW2 Schwerer Gustav Railway Artillery — Brick Block Army22 março 2025
WW2 Schwerer Gustav Railway Artillery — Brick Block Army22 março 2025 -
 KitkaGame's 'Stumble Guys' is an entertaining alternative to Mediatonic's 'Fall Guys' – The Red Ledger22 março 2025
KitkaGame's 'Stumble Guys' is an entertaining alternative to Mediatonic's 'Fall Guys' – The Red Ledger22 março 2025 -
 Triste Naruto Shippuden Online Amino22 março 2025
Triste Naruto Shippuden Online Amino22 março 2025 -
 Anime Taste Testing: Spring 2018 (Part II) – OTAKU LOUNGE22 março 2025
Anime Taste Testing: Spring 2018 (Part II) – OTAKU LOUNGE22 março 2025 -
 Jogo de xadrez com mármore de madeira e materiais clássicos Modelo22 março 2025
Jogo de xadrez com mármore de madeira e materiais clássicos Modelo22 março 2025 -
 Kit 20 Carros Hot Wheels de Corrida Infantil Modelos Sortidos22 março 2025
Kit 20 Carros Hot Wheels de Corrida Infantil Modelos Sortidos22 março 2025 -
 Club Penguin Ninja Desktop , Ninja transparent background PNG clipart22 março 2025
Club Penguin Ninja Desktop , Ninja transparent background PNG clipart22 março 2025 -
 Super Flix Filmes - NOVO DOMÍNIO - Assistir Filmes Online Grátis Dublado e Legendado em HD22 março 2025
Super Flix Filmes - NOVO DOMÍNIO - Assistir Filmes Online Grátis Dublado e Legendado em HD22 março 2025
