Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's
Por um escritor misterioso
Last updated 13 fevereiro 2025

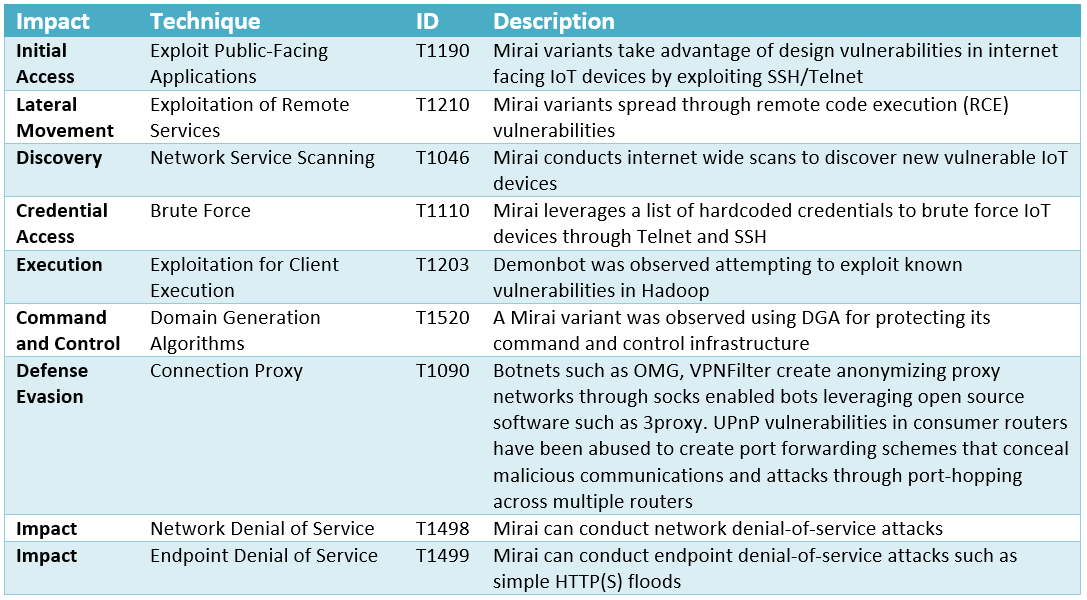
We analyzed tactics, techniques, and procedures utilized by threat actors of the FireEye’s stolen Red Team Tools. Attackers heavily used various defense evasion techniques.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
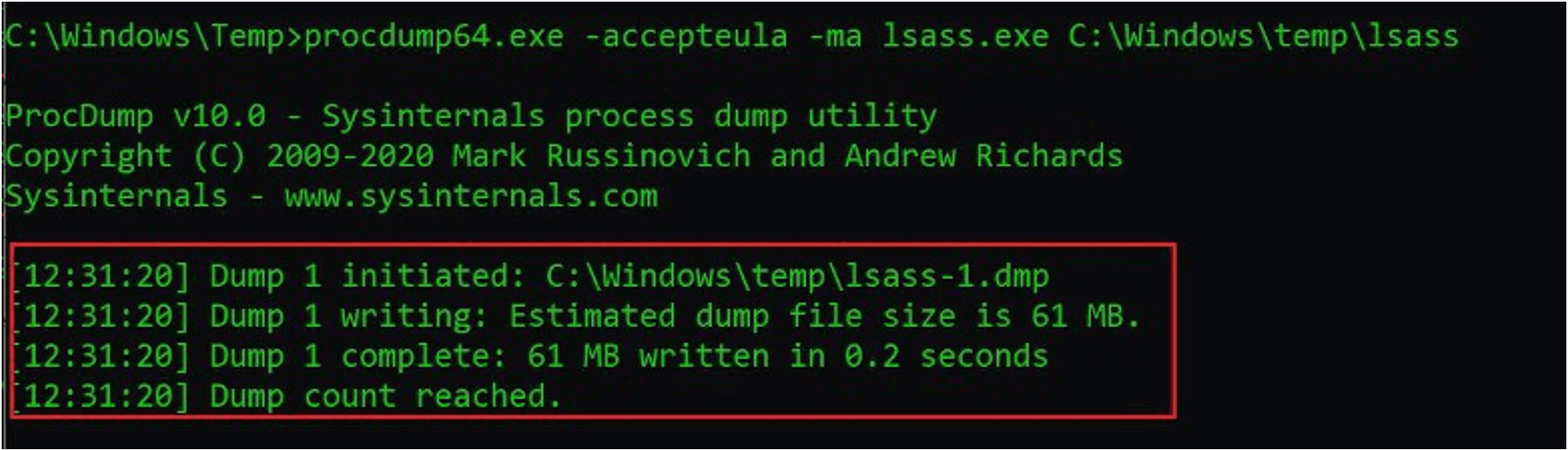
Protecting Against HAFNIUM With FireEye Endpoint Security Process
Threat Reports Overview - Forescout

Not So Cozy: An Uncomfortable Examination of a Suspected APT29

Following FireEye Hack, Ensure These 16 Bugs Are Patched
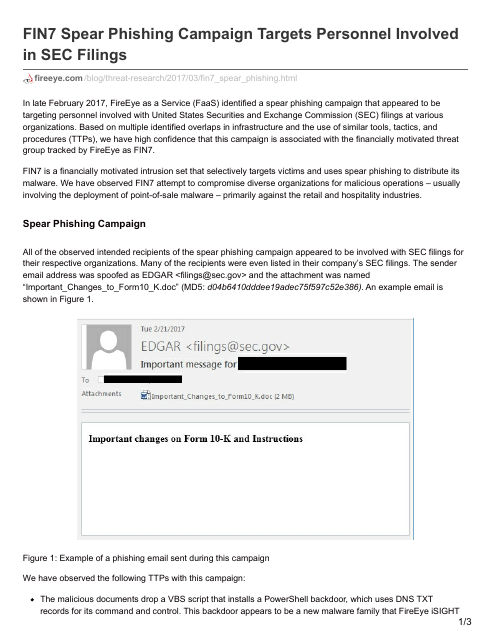
FIN7 Spear Phishing Campaign Targets Personnel Involved in SEC
Applied Sciences, Free Full-Text

TRITON Actor TTP Profile, Custom Attack Tools, Detections, and

Inside the Mind of a Cyber Attacker
Tactics, Techniques and Procedures

FireEye Hack Turns into a Global Supply Chain Attack – Radware Blog
Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's
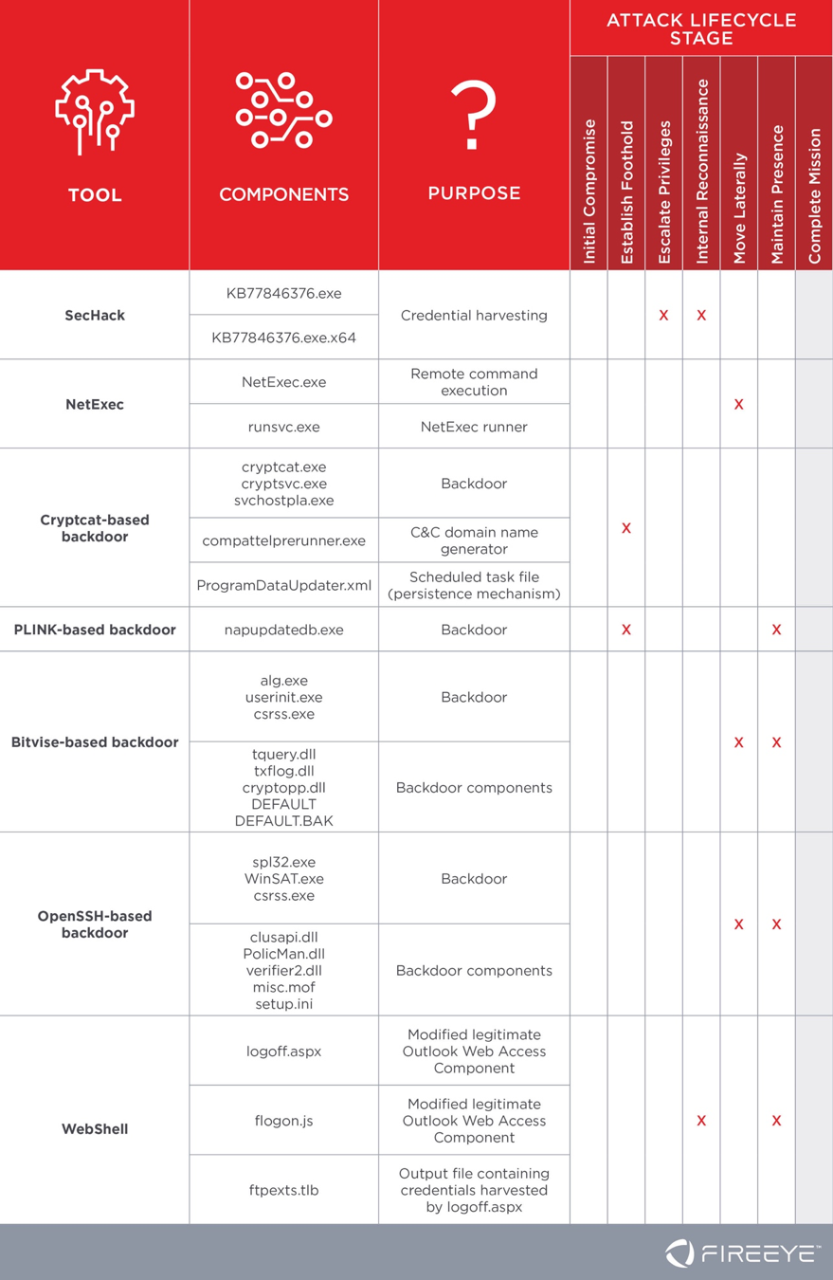
TRITON Actor TTP Profile, Custom Attack Tools, Detections, and

AutoTTP - Automated Tactics Techniques & Procedures
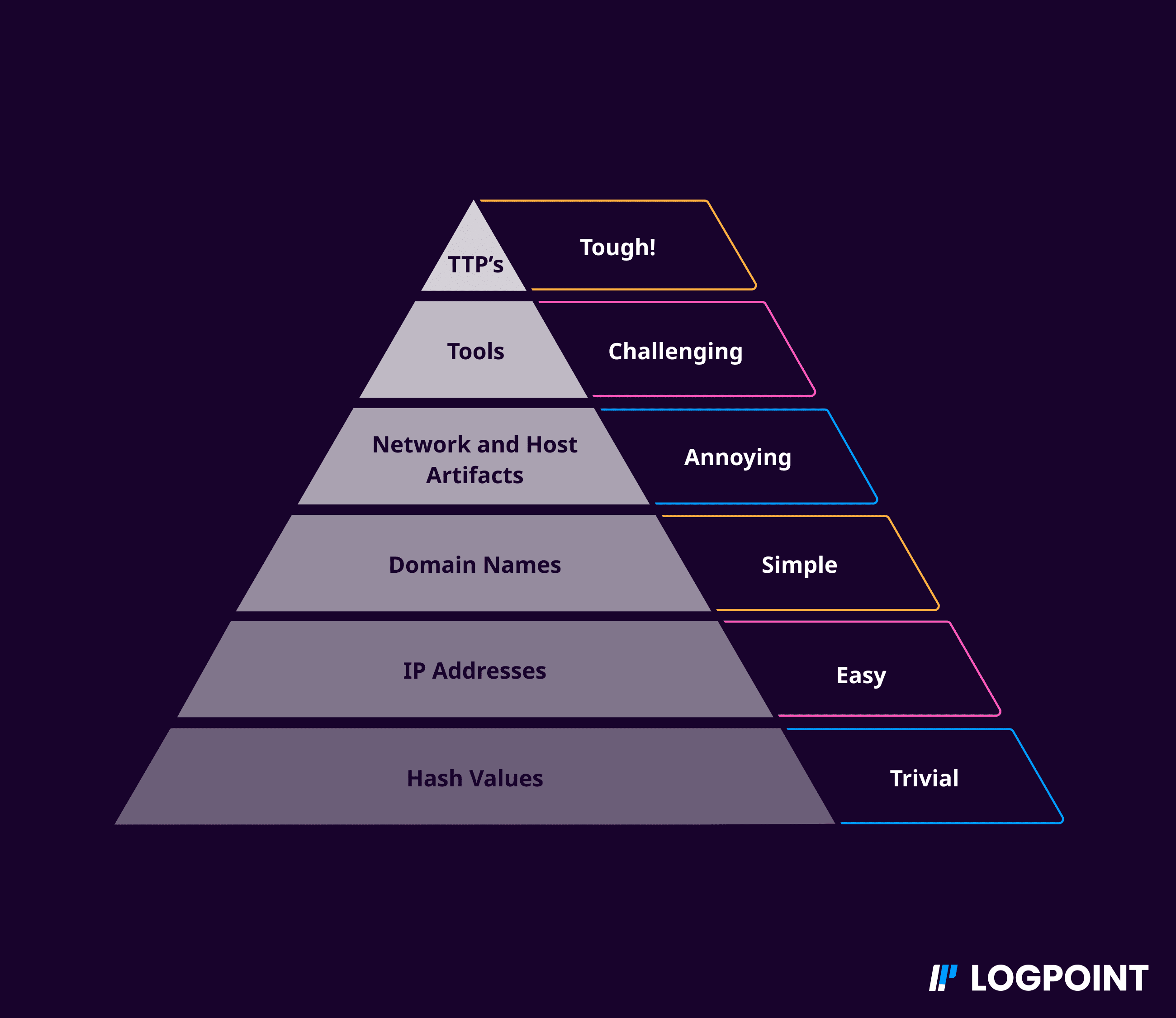
Behavioral analysis in security - Logpoint

FireEye offers proactive OT environment protection with latest
Recomendado para você
-
 meu cachorro morreu e agora não tenho dinheiro para spoofer no13 fevereiro 2025
meu cachorro morreu e agora não tenho dinheiro para spoofer no13 fevereiro 2025 -
 Risk Intelligence & Device Fingerprinting Solution13 fevereiro 2025
Risk Intelligence & Device Fingerprinting Solution13 fevereiro 2025 -
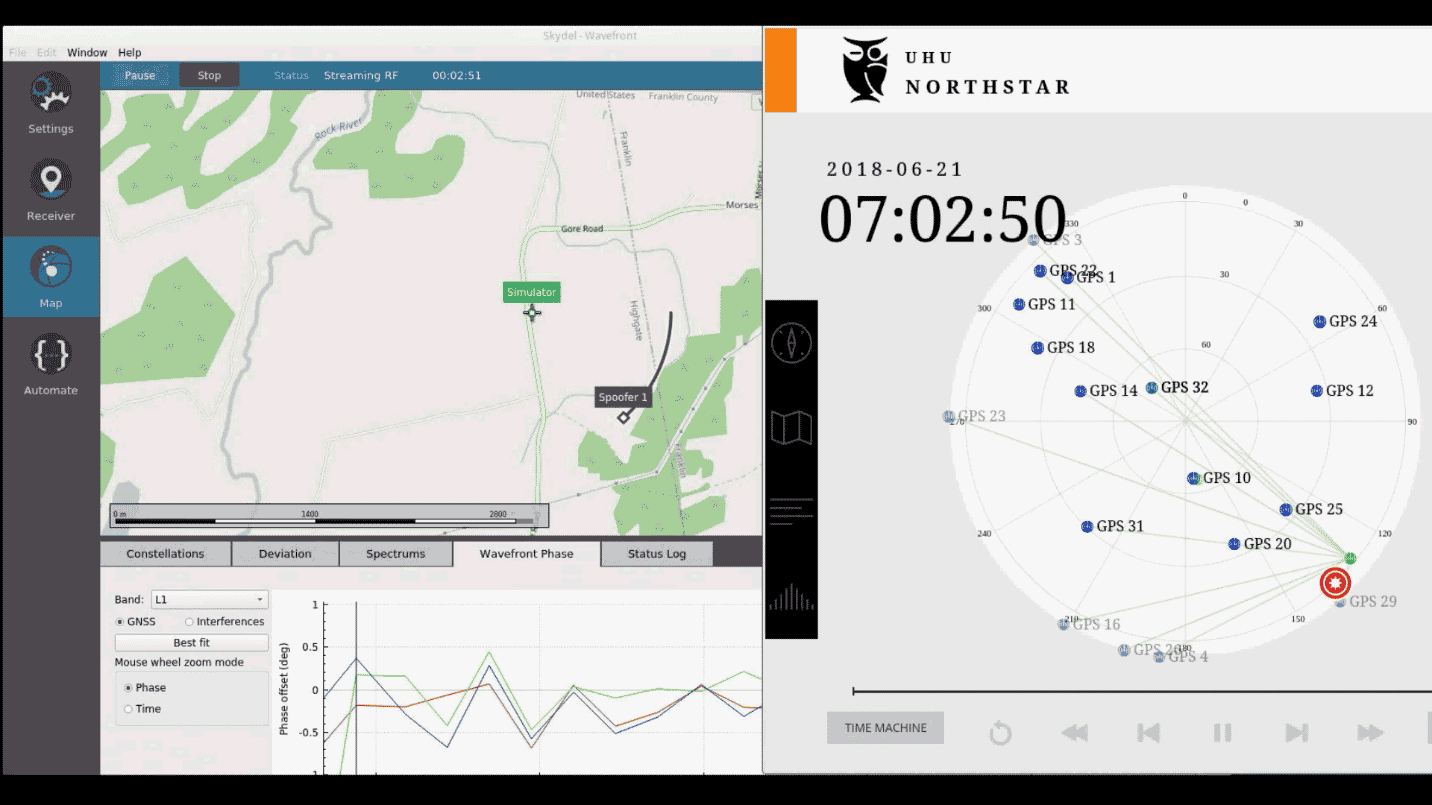 An Engineer's Guide to CRPA Testing - Safran - Navigation & Timing13 fevereiro 2025
An Engineer's Guide to CRPA Testing - Safran - Navigation & Timing13 fevereiro 2025 -
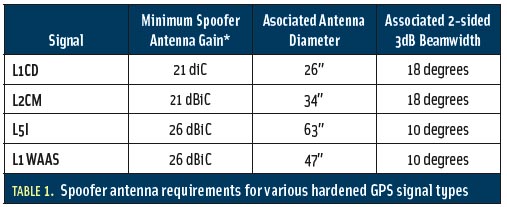 Spoofs, Proofs & Jamming - Inside GNSS - Global Navigation13 fevereiro 2025
Spoofs, Proofs & Jamming - Inside GNSS - Global Navigation13 fevereiro 2025 -
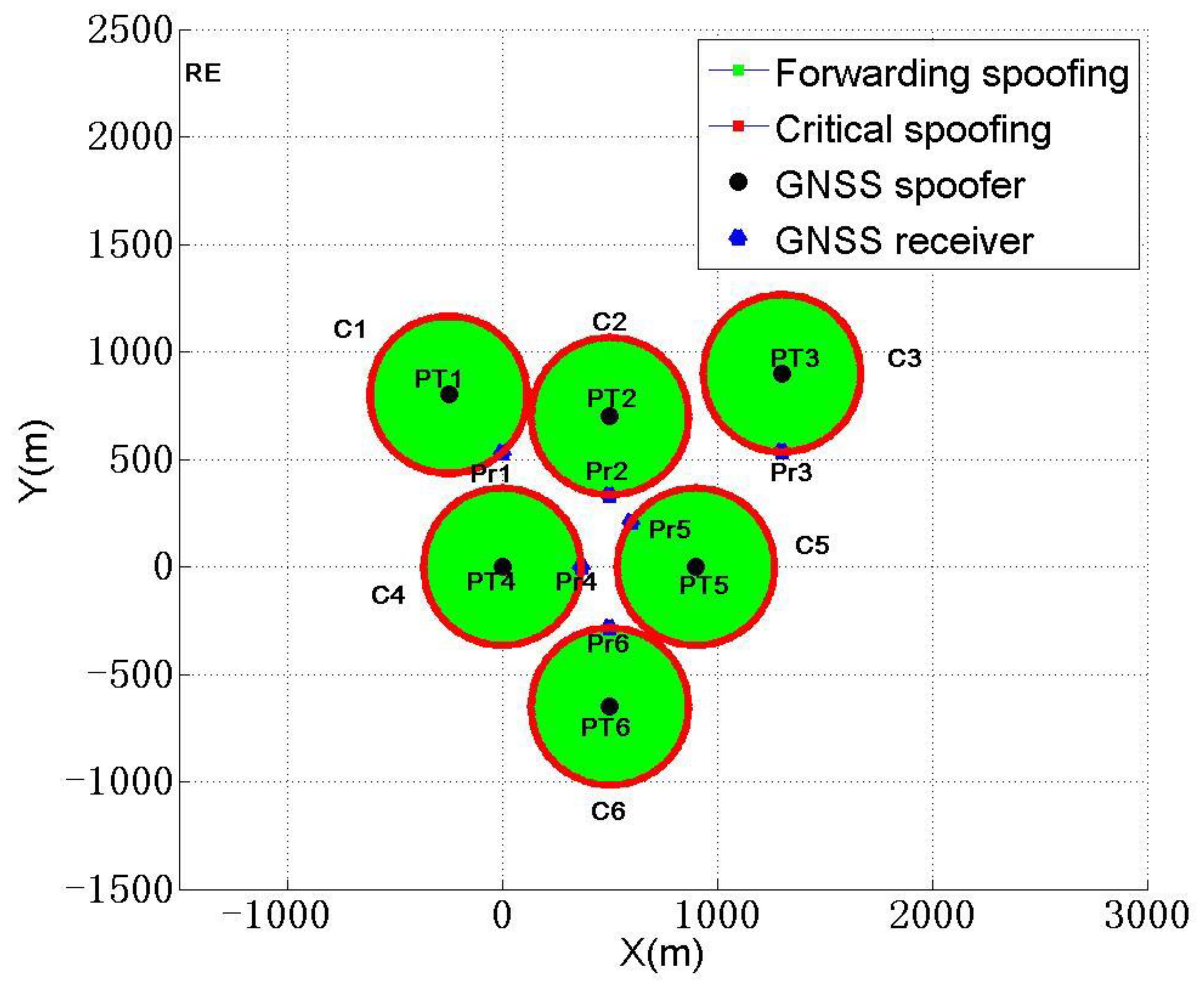 Sensors, Free Full-Text13 fevereiro 2025
Sensors, Free Full-Text13 fevereiro 2025 -
Location Guard13 fevereiro 2025
-
 Simply Click to Change Your Location in Pokémon GO13 fevereiro 2025
Simply Click to Change Your Location in Pokémon GO13 fevereiro 2025 -
 Precision Digital Webinars13 fevereiro 2025
Precision Digital Webinars13 fevereiro 2025 -
 11 Types of Spoofing Attacks Every Security Professional Should13 fevereiro 2025
11 Types of Spoofing Attacks Every Security Professional Should13 fevereiro 2025 -
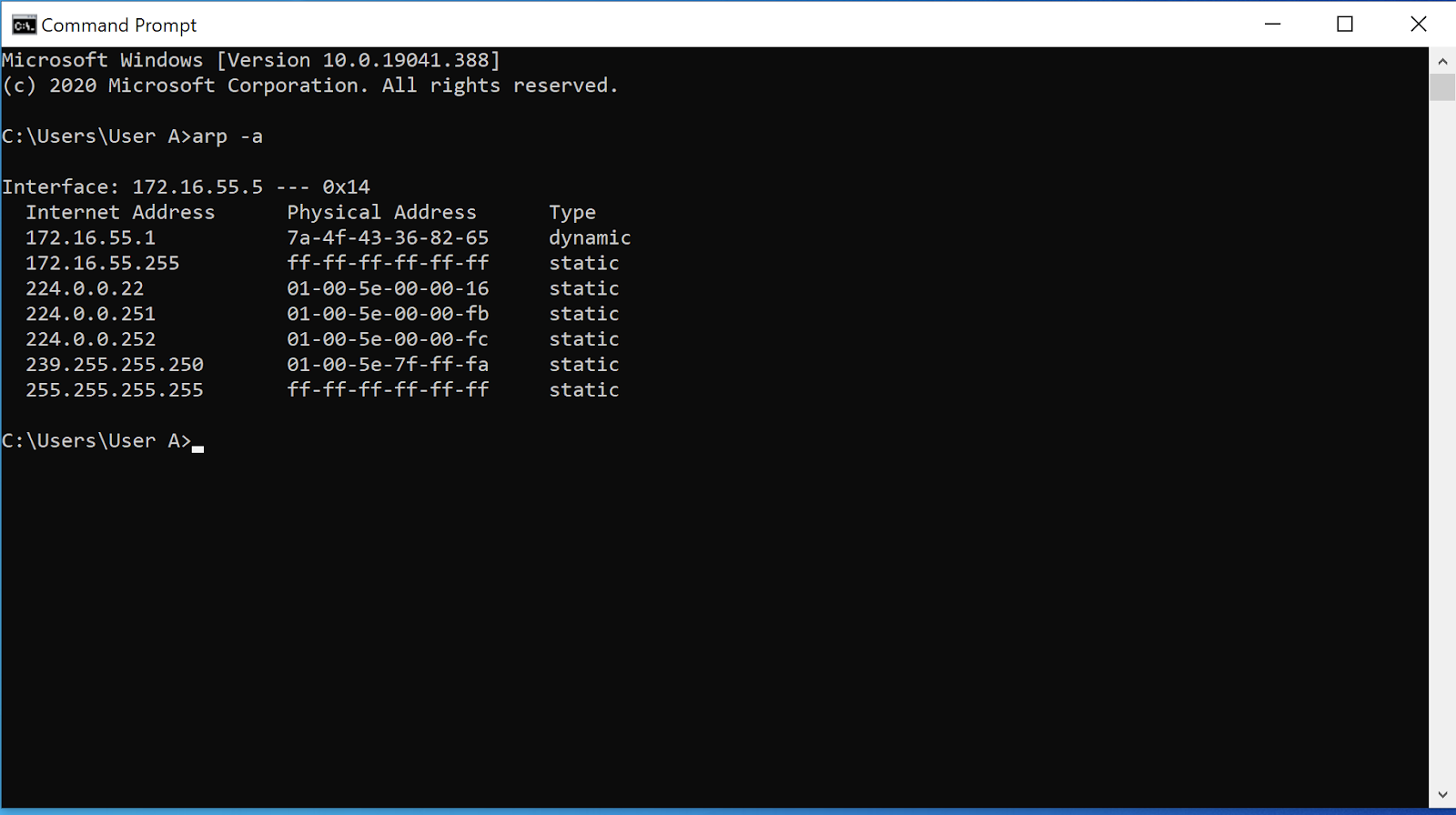 ARP Poisoning: What it is & How to Prevent ARP Spoofing Attacks13 fevereiro 2025
ARP Poisoning: What it is & How to Prevent ARP Spoofing Attacks13 fevereiro 2025
você pode gostar
-
 Ace Combat 7 Skies Unknown - Ps4 - Turok Games - Só aqui tem13 fevereiro 2025
Ace Combat 7 Skies Unknown - Ps4 - Turok Games - Só aqui tem13 fevereiro 2025 -
 Cartoon Characters png download - 1000*796 - Free Transparent Bioshock Infinite png Download. - CleanPNG / KissPNG13 fevereiro 2025
Cartoon Characters png download - 1000*796 - Free Transparent Bioshock Infinite png Download. - CleanPNG / KissPNG13 fevereiro 2025 -
 Traia De Frente Rosa Argolada Para Mula e Cavalo Cabeçada e13 fevereiro 2025
Traia De Frente Rosa Argolada Para Mula e Cavalo Cabeçada e13 fevereiro 2025 -
Watch Ace Attorney - Crunchyroll13 fevereiro 2025
-
 Man with black beard, J. Cole Holding Face, music stars, j. cole13 fevereiro 2025
Man with black beard, J. Cole Holding Face, music stars, j. cole13 fevereiro 2025 -
 Prince of Persia: Warrior Within (PC DVD Game) Define your own13 fevereiro 2025
Prince of Persia: Warrior Within (PC DVD Game) Define your own13 fevereiro 2025 -
 Bola basquete silenciosa para ambientes internos com 5 peças – Bola treinamento silenciosa para ambientes internos, bola espuma alta densida, macia, leve, fácil segurar, bola silenciosa, adequada para vários ambientes internos que13 fevereiro 2025
Bola basquete silenciosa para ambientes internos com 5 peças – Bola treinamento silenciosa para ambientes internos, bola espuma alta densida, macia, leve, fácil segurar, bola silenciosa, adequada para vários ambientes internos que13 fevereiro 2025 -
 PICTEK PC306 Professional Gaming Mouse 16000DPI Gaming Programming Mouse Adjustable Light Synchronizatio For Mouse Gamer LOL CS - AliExpress13 fevereiro 2025
PICTEK PC306 Professional Gaming Mouse 16000DPI Gaming Programming Mouse Adjustable Light Synchronizatio For Mouse Gamer LOL CS - AliExpress13 fevereiro 2025 -
 FOUR MOVES?! - FNAF World Redacted - Part 113 fevereiro 2025
FOUR MOVES?! - FNAF World Redacted - Part 113 fevereiro 2025 -
 É fã de ovo cozido? O tempo exato de cozedura e mais 5 dicas13 fevereiro 2025
É fã de ovo cozido? O tempo exato de cozedura e mais 5 dicas13 fevereiro 2025