Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Last updated 15 fevereiro 2025
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

How did I create hacking rig for ethical hacking. Based on VMware with Tesla M60. #infosec #hacking #pentest #pentesting #redteam #hackthebox #tryhackme #linux4hackers #ctf #kali #parrotos #linux #godaddy #linux4hackers – Tips and

DNC Hacks: How Spear Phishing Emails Were Used

Infrastructure Hacking: Telnet Protocol » Hacking Lethani

Iranian hacker claims he acted alone in stealing digital SSL certificates, Hacking

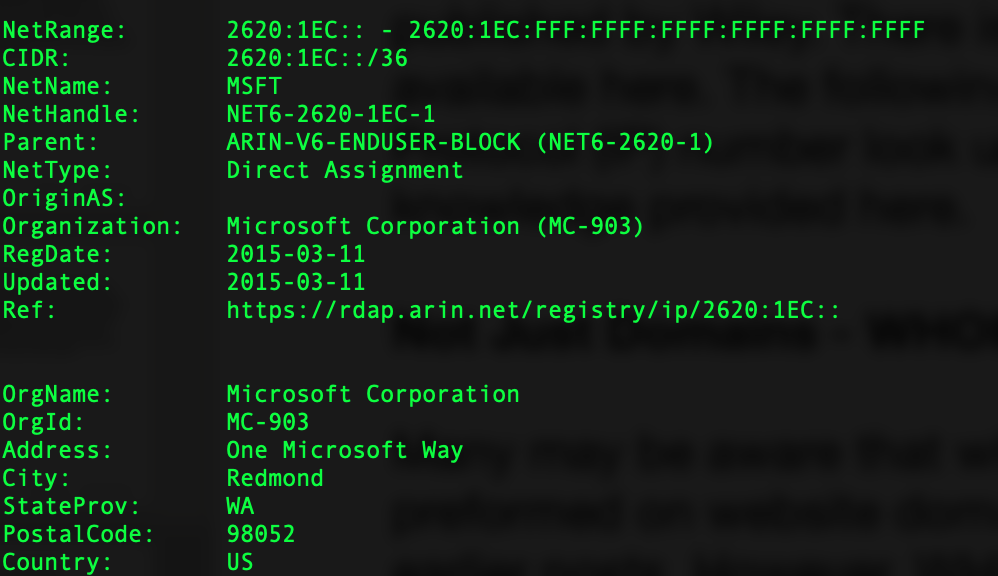
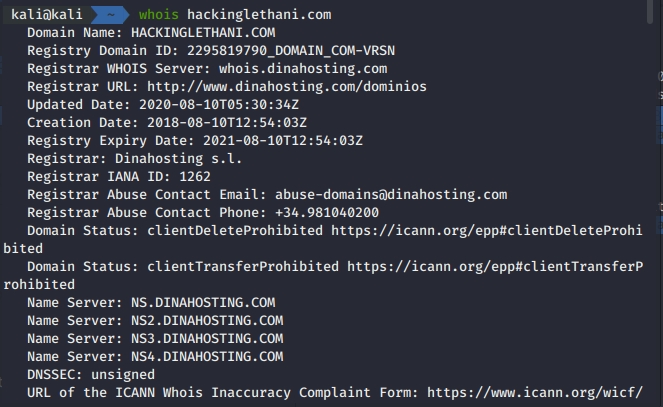
Infrastructure Hacking: WHOIS Protocol » Hacking Lethani

Cyber Security & Ethical Hacking - Whois ( “who owns a domain?”)

Hackers breached Greece's top-level domain registrar

Cyber Security & Ethical Hacking - Whois ( “who owns a domain?”)
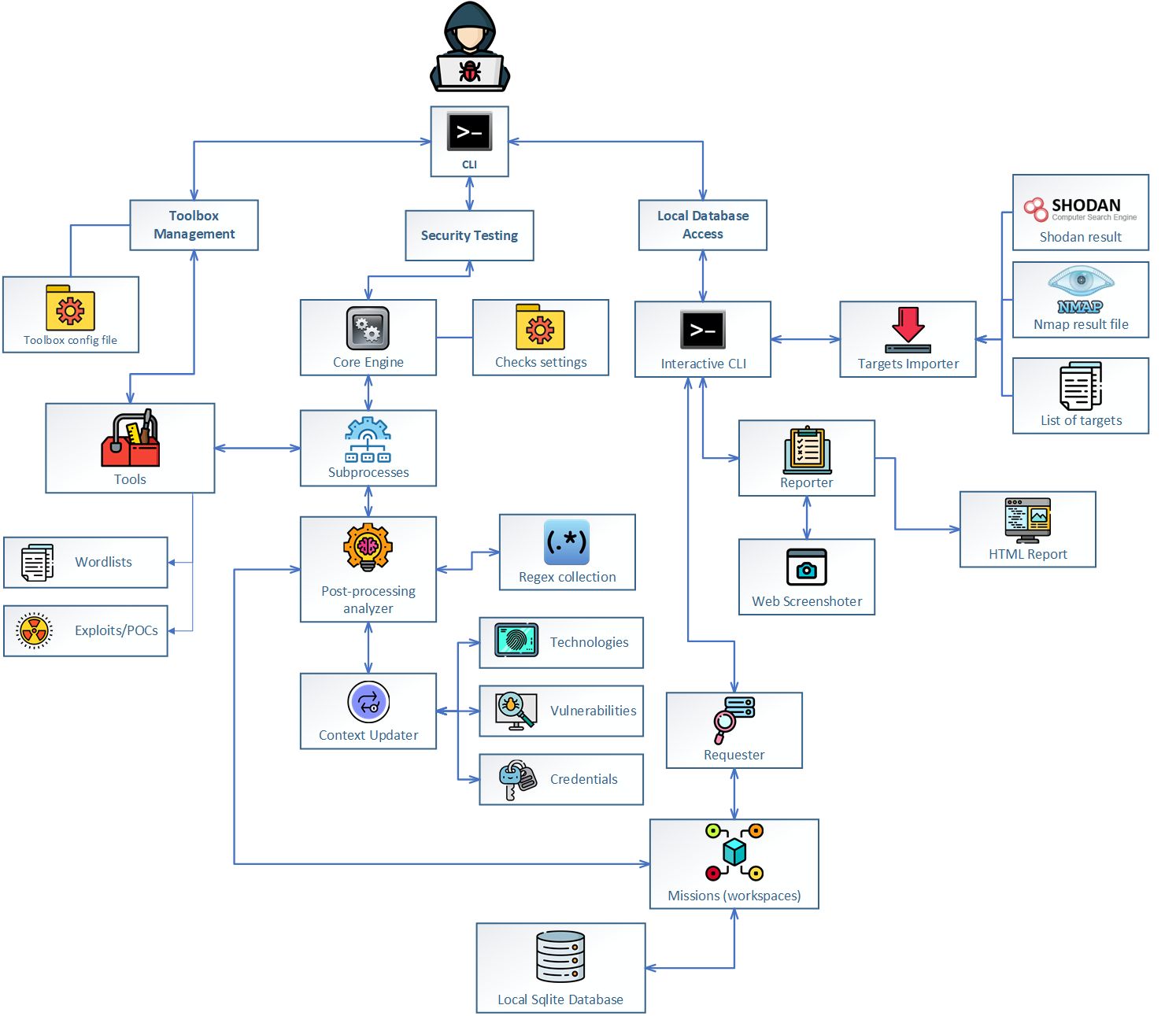
Jok3r v3 BETA 2 - Network and Web Pentest Automation Framework
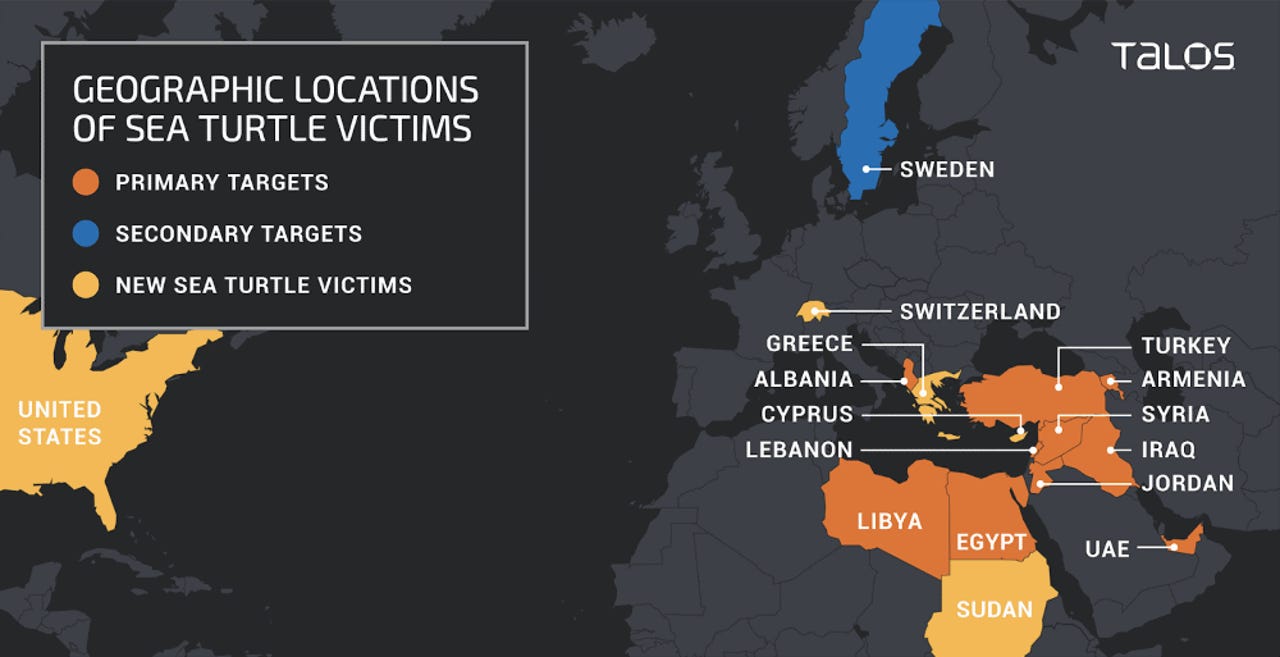
Hackers breached Greece's top-level domain registrar

Best platforms to learn ethical hacking! - Intigriti

Hackbun

Tips for Investigating Cybercrime Infrastructure
Recomendado para você
-
 Domain Names & Identity for Everyone15 fevereiro 2025
Domain Names & Identity for Everyone15 fevereiro 2025 -
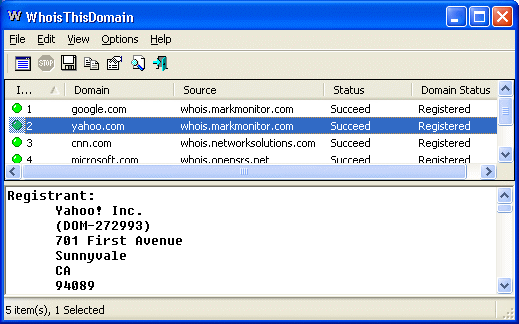 Domain name search tool (Whois) for Windows15 fevereiro 2025
Domain name search tool (Whois) for Windows15 fevereiro 2025 -
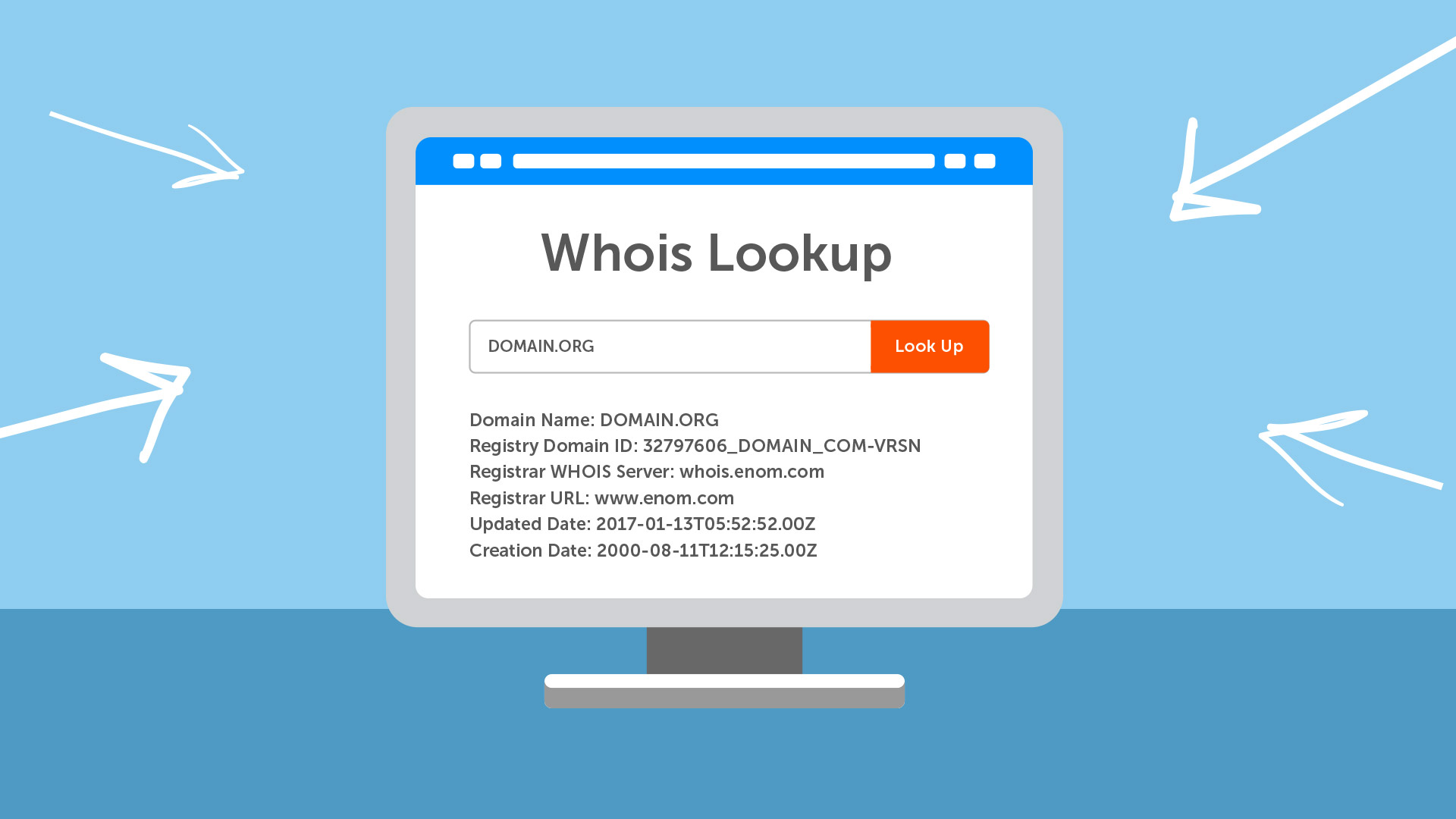 The WHOIS Database15 fevereiro 2025
The WHOIS Database15 fevereiro 2025 -
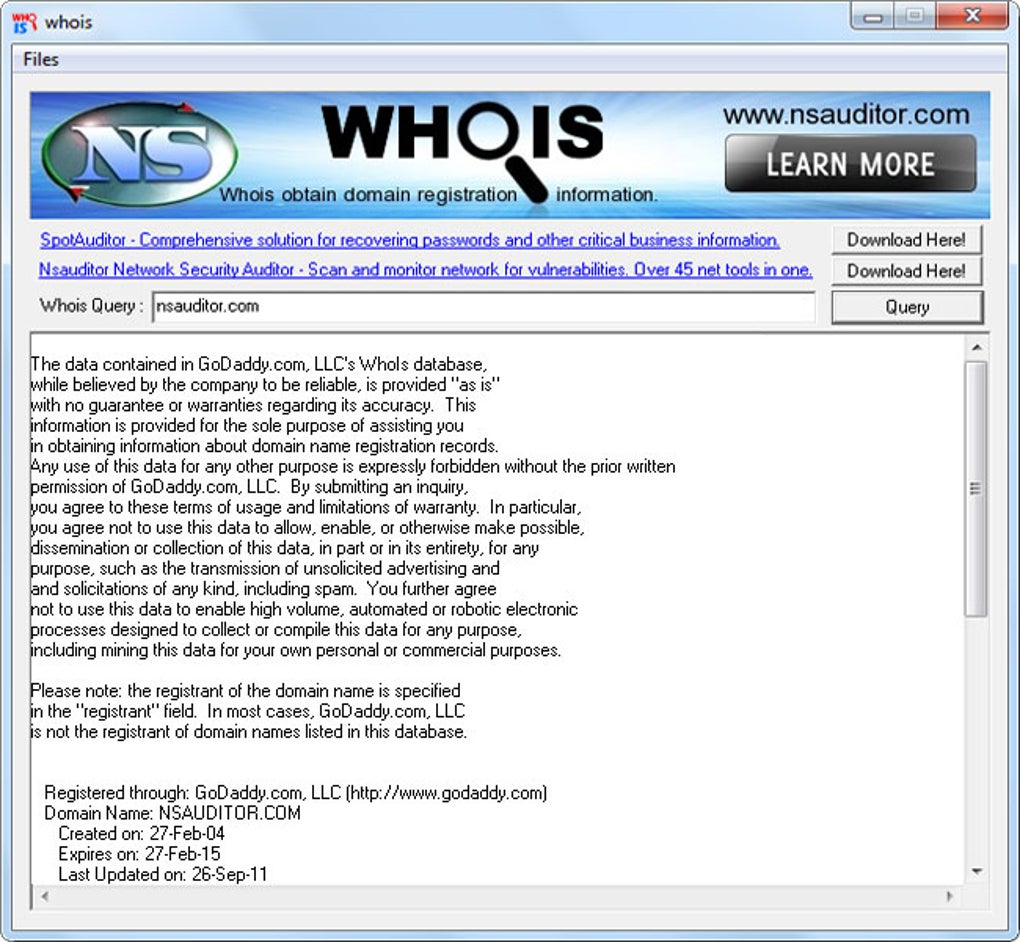 Whois - Download15 fevereiro 2025
Whois - Download15 fevereiro 2025 -
 How To Find Whois Domain Information from Command Line15 fevereiro 2025
How To Find Whois Domain Information from Command Line15 fevereiro 2025 -
 Finding Domain and Registrations Details With Wix Whois Lookup15 fevereiro 2025
Finding Domain and Registrations Details With Wix Whois Lookup15 fevereiro 2025 -
Internet Protocol(IP) WHOIS15 fevereiro 2025
-
 whois15 fevereiro 2025
whois15 fevereiro 2025 -
 WhoIs v2.7, Karen's Power Tools15 fevereiro 2025
WhoIs v2.7, Karen's Power Tools15 fevereiro 2025 -
Whois Icon15 fevereiro 2025
você pode gostar
-
 Doors Entities Figure Rush Ambush A-60 A-90 A-120 Seek Stare El Goblino Dupe Halt Jeff Bob Eyes Screech Jack Glitch Timothy Shadow Window | Art Print15 fevereiro 2025
Doors Entities Figure Rush Ambush A-60 A-90 A-120 Seek Stare El Goblino Dupe Halt Jeff Bob Eyes Screech Jack Glitch Timothy Shadow Window | Art Print15 fevereiro 2025 -
 How to Delete a Discord Server in 2022 (Guide)15 fevereiro 2025
How to Delete a Discord Server in 2022 (Guide)15 fevereiro 2025 -
How to mod on GTA V on a PS3 without paying for a mod menu - Quora15 fevereiro 2025
-
 Fonte de Alimentação Gamemax GP650 650W 80 Plus Bronze PFC Ativo - EletroTrade15 fevereiro 2025
Fonte de Alimentação Gamemax GP650 650W 80 Plus Bronze PFC Ativo - EletroTrade15 fevereiro 2025 -
 Ragnarok Online Knight Ragnarök Lord Wiki, Knight transparent background PNG clipart15 fevereiro 2025
Ragnarok Online Knight Ragnarök Lord Wiki, Knight transparent background PNG clipart15 fevereiro 2025 -
 🔴 Acesso antecipado de Assassin's Creed Mirage! #115 fevereiro 2025
🔴 Acesso antecipado de Assassin's Creed Mirage! #115 fevereiro 2025 -
 Cheap Fireworks Online, Cobra Kiss15 fevereiro 2025
Cheap Fireworks Online, Cobra Kiss15 fevereiro 2025 -
Jogue Fácil15 fevereiro 2025
-
 Fukigen na Mononokean Image by Pierrot Plus #3974526 - Zerochan15 fevereiro 2025
Fukigen na Mononokean Image by Pierrot Plus #3974526 - Zerochan15 fevereiro 2025 -
 tree knife murder mystery value|TikTok Search15 fevereiro 2025
tree knife murder mystery value|TikTok Search15 fevereiro 2025