Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's Red Team Tools
Por um escritor misterioso
Last updated 16 março 2025

We analyzed tactics, techniques, and procedures utilized by threat actors of the FireEye’s stolen Red Team Tools. Attackers heavily used various defense evasion techniques.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
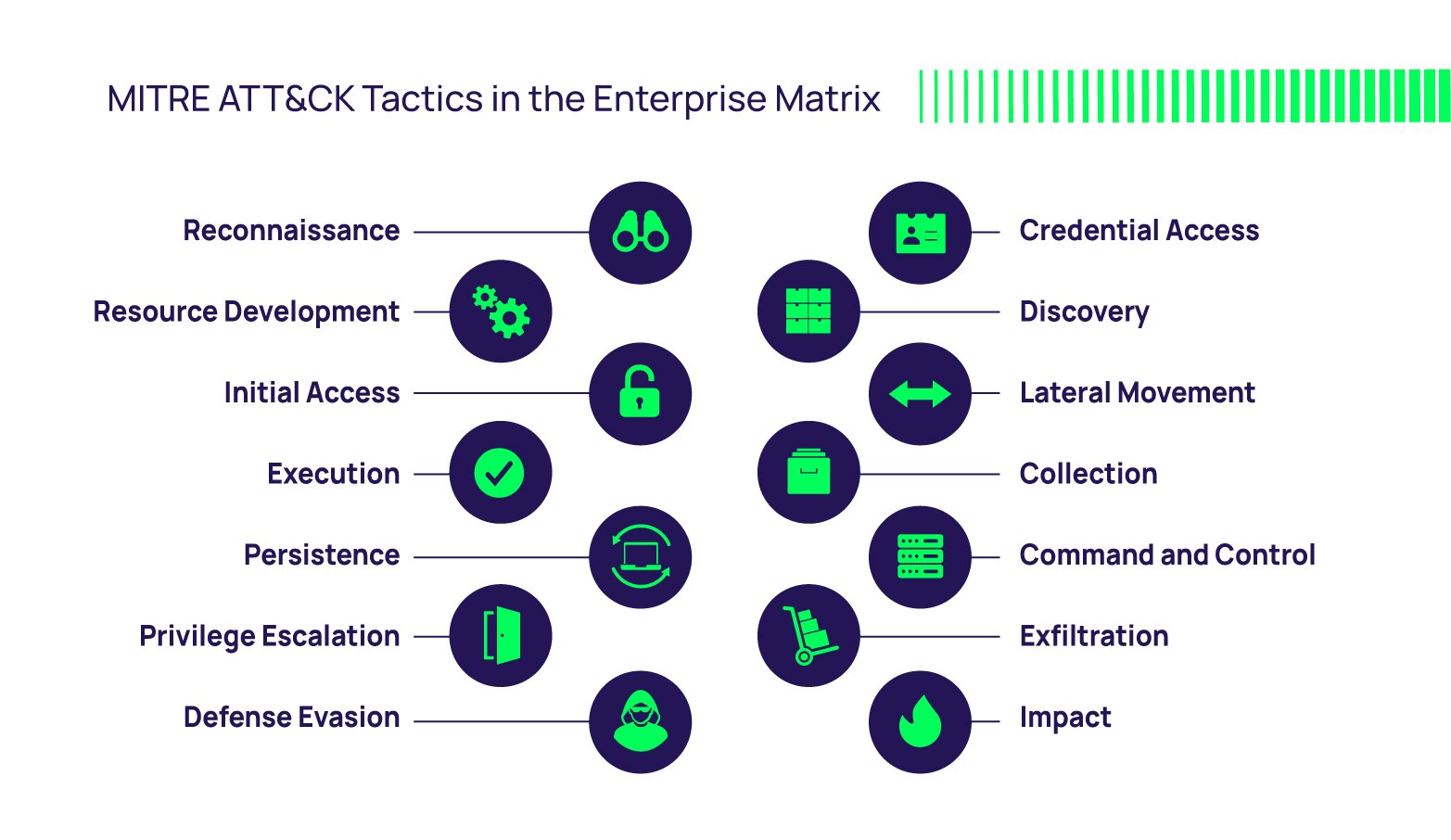
The MITRE ATT&CK Framework

Tactics, Techniques and Procedures of FireEye Red Team Tools

100 Best Free Red Team Tools in 2023 - Cyber Security News

Tactics, Techniques and Procedures of FireEye Red Team Tools

Adversary Emulation and Red Team Exercises - EDUCAUSE
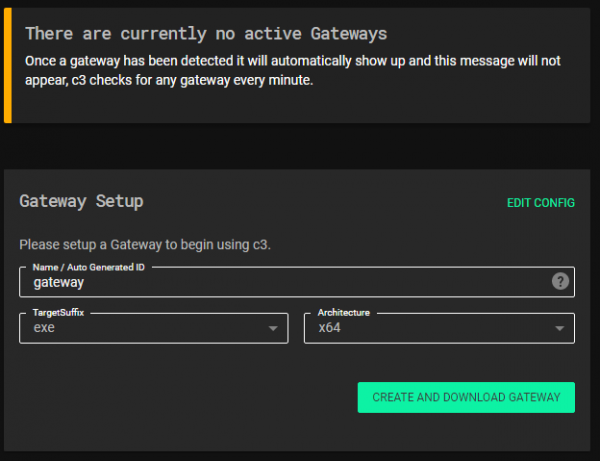
C3 WithSecure™ Labs

Red Team Tools Detection and Alerting

Red Team Assessment, Dubai

SolarWinds Post-Compromise Hunting with Azure Sentinel - Microsoft
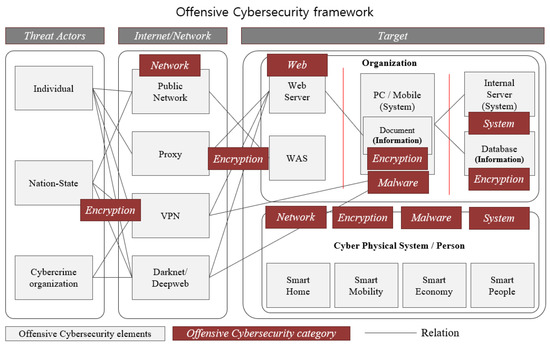
Applied Sciences, Free Full-Text

TTPs Within Cyber Threat Intelligence

GitHub - A-poc/RedTeam-Tools: Tools and Techniques for Red Team
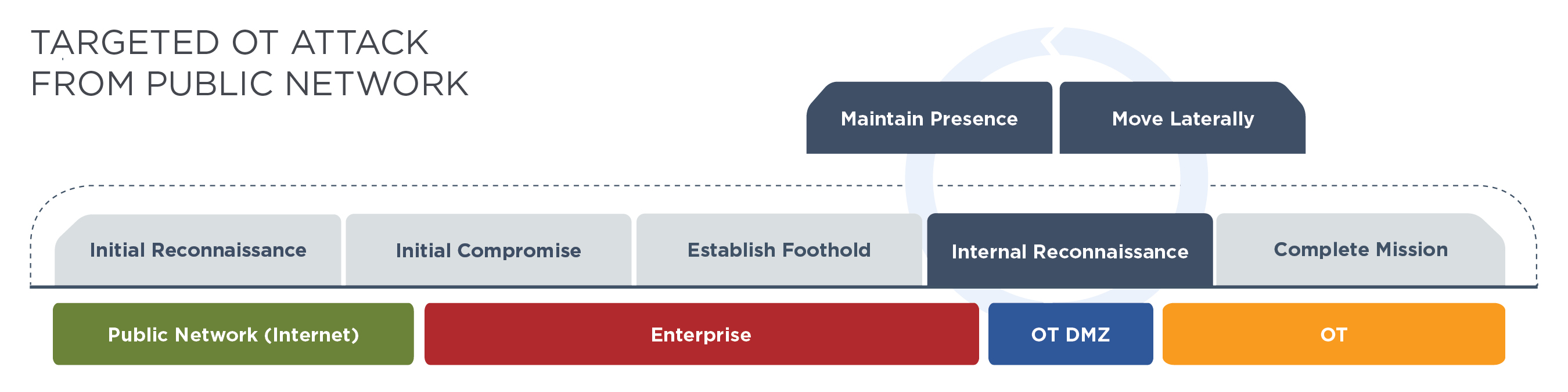
Hacking Operational Technology for Defense

Following FireEye Hack, Ensure These 16 Bugs Are Patched

Using Microsoft 365 Defender to protect against Solorigate
Recomendado para você
-
Raj Echambadi on LinkedIn: Illinois Tech's CARNATIONS Receives $1016 março 2025
-
 Beware of Spoof Websites - RCB Bank16 março 2025
Beware of Spoof Websites - RCB Bank16 março 2025 -
 Visitor's Guide University of Arkansas16 março 2025
Visitor's Guide University of Arkansas16 março 2025 -
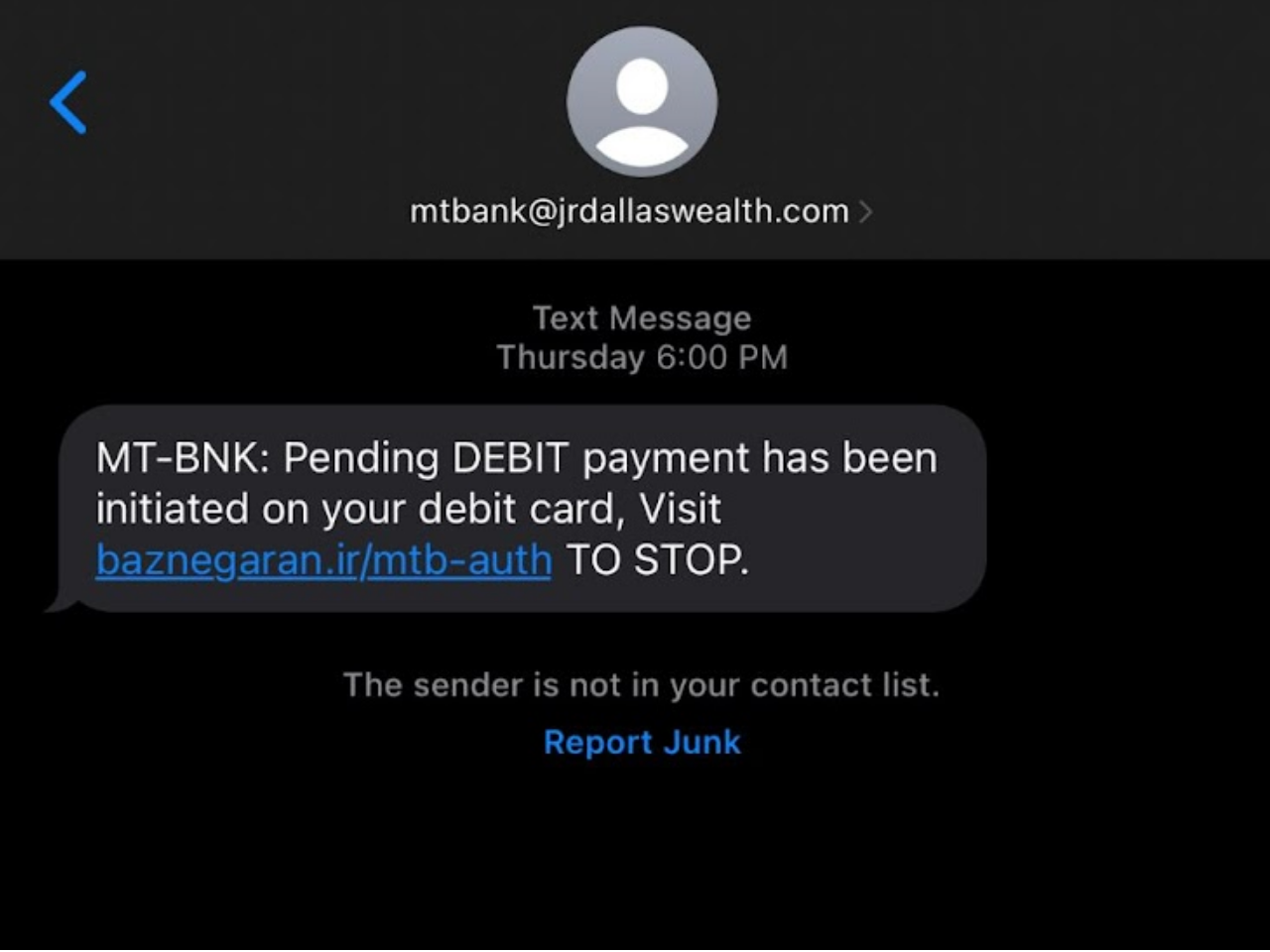 What Is Spoofing In Cybersecurity?16 março 2025
What Is Spoofing In Cybersecurity?16 março 2025 -
 GootBot - Gootloader's new approach to post-exploitation16 março 2025
GootBot - Gootloader's new approach to post-exploitation16 março 2025 -
 Device Fingerprinting - SEON Docs16 março 2025
Device Fingerprinting - SEON Docs16 março 2025 -
 US7814533B2 - Secure customer interface for Web based data management - Google Patents16 março 2025
US7814533B2 - Secure customer interface for Web based data management - Google Patents16 março 2025 -
 Fortune India: Business News, Strategy, Finance and Corporate Insight16 março 2025
Fortune India: Business News, Strategy, Finance and Corporate Insight16 março 2025 -
 redENGINE – FiveM Spoofer16 março 2025
redENGINE – FiveM Spoofer16 março 2025 -
 Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's16 março 2025
Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's16 março 2025
você pode gostar
-
 Cut the Rope GOLD 3.7.0 Apk + Mod for android16 março 2025
Cut the Rope GOLD 3.7.0 Apk + Mod for android16 março 2025 -
 Psst… Its Screech Roblox Doors Unisex T-Shirt - Teeruto16 março 2025
Psst… Its Screech Roblox Doors Unisex T-Shirt - Teeruto16 março 2025 -
 One big dumb lizard down, just one left, a bit of a bittersweet feeling to be reaching the end of this game : r/MonsterHunterWorld16 março 2025
One big dumb lizard down, just one left, a bit of a bittersweet feeling to be reaching the end of this game : r/MonsterHunterWorld16 março 2025 -
fastest subway surfer run|TikTok Search16 março 2025
-
 LIVRETO PARA COLORIR E APRENDER - VAMOS CUIDAR DO MEIO AMBIENTE?16 março 2025
LIVRETO PARA COLORIR E APRENDER - VAMOS CUIDAR DO MEIO AMBIENTE?16 março 2025 -
 Tommy Hilfiger Watches for Men - Shop Now on FARFETCH16 março 2025
Tommy Hilfiger Watches for Men - Shop Now on FARFETCH16 março 2025 -
Drawing Goku, Vegeta and Broly - Dragon Ball Super: Broly Special, ➡️Quer aprender a Desenhar? ➡️(Clique no link abaixo) aproveite 3 Super Bônus grátis ➡️ By Como desenhar16 março 2025
-
Detonado Assassin's Creed II, PDF, Leonardo da Vinci16 março 2025
-
 5 Surprise Games We'd Like to See at the Xbox Developer Direct Livestream16 março 2025
5 Surprise Games We'd Like to See at the Xbox Developer Direct Livestream16 março 2025 -
 Encouragement of Climb Season 3 Gets New Visual, Summer of 2018 Premiere - Anime Herald16 março 2025
Encouragement of Climb Season 3 Gets New Visual, Summer of 2018 Premiere - Anime Herald16 março 2025



